If you have a website that provides a service to customers outside your company, it may have a digital certificate that is public rooted. This means that the chain of trust leads to a root certificate issued by a well-known certificate authority (CA) that has already been trusted by your users' browsers and other key application technologies (e.g. Java). By using a public trunk, you can instantly achieve universal trust in your entire user base.
You may also have a number of other servers that are not externally targeted and do not require publicly rooted certificates. However, these servers may still need authentication, signing, and functionality to establish a secure TLS session with other internal servers or applications. The root of trust for these servers would be a private certification authority (CA). A separate certification body that is part of the cloud-based Sectigo Private PKI- offer.
With our private PKI solution you can mark the certificates for your servers, devices and users. Because the purpose of this certification authority is to serve only your company, it provides more precise control when this PKI infrastructure is used for internal user authentication. For this reason, private PKI is extremely popular for deployment in corporate IT as well as in cloud-native DevOps and Internet of Things (IoT) environments.
Three deployment scenarios
There are three deployment architectures to consider to use Sectigo Private PKI:
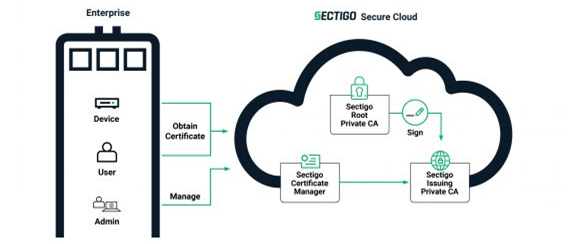
- Sectigo hosts the private root certification authority and the issuing certification authority (s) in the cloud for you.
- Your organization hosts the private root certification authority of your choice and Sectigo hosts the issuing certification authority (s) for you.
- Or Sectigo hosts the private root certification authority and your organization hosts the issuing certification authorities
Many of our customers prefer option 1 because all operational aspects of PKI, including hosting, maintenance, security and compliance, are handled by Sectigo. You simply obtain and install certificates from us and make them available in your environment. Some customers may already have a private root CA, or their corporate security policy may require that the root CA be in their area. In this case, Sectigo can host and manage the issuing certification authorities that are signed by their local root certification authority.
Since the majority of the work is done at the issuing certification body, they are relieved of many everyday tasks. In the third situation mentioned above, a certification authority (e.g. Microsoft certification authority, HashiCorp Vault PKI instance or Kubernetes certification authority) may be active in your environment and integrated into your applications. You can significantly improve your security situation by hosting an offline root CA with keys stored in a Hardware Security Module (HSM) in an industry-standard data center, and signing your existing CA, which will then issue and manage end-user certificates and devices.
We can help you choose the option that best suits your situation and help you implement the deployment architecture you choose. Figures 1, 2 and 3 show all three scenarios.



IT and DevOps friendly private PKI
You will likely use trusted certificates in your AWS, Azure, or other cloud environment for container-to-container and application-to-application authentication and secure communication between them. Sectigo Private PKI is integrated into the most common DevOps tools, so that when you roll out your infrastructure and applications automatically, you can seamlessly register certificates from Sectigo Private PKI and manage their lifecycle. To ensure that your software is not tampered with, you should also code your containers and other applications with code signatures, which can also come from the same PKI infrastructure.
Mit dem Aufkommen der Cloud-freundlichen Mikrodienstarchitektur können Ihre Dienste kommen und gehen, was ein hohes Volumen und kurzlebige Zertifikate erfordert. Sectigo Private PKI ist in der Lage, Zertifikate mit einem kurzen Lebenszyklus auszustellen und zu verwalten. Unser Lizenzierungsschema unterstützt dieses Geschäftsmodell, um es für Sie kosteneffizient zu gestalten.
Automation-oriented solution
Automation plays a key role in our architecture. Sectigo Private PKI supports you in the end-to-end automation of issuing and installing certificates.
We support industry-standard protocols such as registration via secure transport (EST) and the Simple Certificate Enrollment Protocol (SCEP) and work on integration with third-party tools, e.g. B. Kubernetes Cert-Manager, HashiCorp Terraform and Vault, Ansible. Puppet, cook and others. In Microsoft Windows environments you can use our automatic registration function to issue certificates from Sectigo Private PKI. For non-Microsoft companies, you can use other supported tools that have been tested with our private PKI to manage certificates for them.
This latest blog, " When it comes to automating SSL certificates Sectigo offers many options, “ contains useful ones Information about the suite of automation tools that Sectigo uses to reduce the manual work of administrators.
Central Management Console
Our customers rarely prefer to go to two different providers to get their public and private certificates. For this reason, we have designed our system so that you can manage everything from a central console, which can be used as a Enterprise Certificate Manager is called . The administrator's experience is the same regardless of the type of certificates you manage. All of your certificates are displayed in the central console with their status and expiry date. Certificate Manager can recognize all your certificates, even if they are not from Sectigo / Comodo, and generate reports on them.
We have other exciting plans to give you a comprehensive overview of your private PKI, public SSL and corporate IoT certificates. Contact us for more information.